


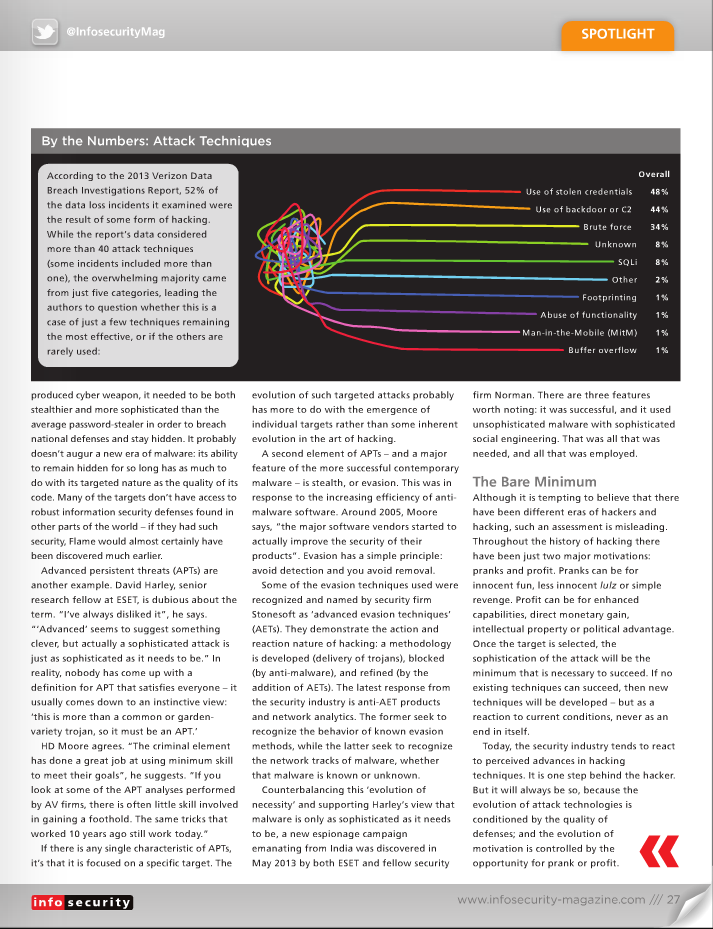

http://www.infosecurity-magazine.com/view/34416/hacking-same-same-but-different/ Hacking: Same Same but Different Hacking technologies have changed little over the years, argues Kevin Townsend, but the opportunities for hackers have changed dramatically There is a common perception that hacking originated as a fun activity, turned into a criminal business, and is now evolving into cyber warfare – and that during this process hacking techniques have become increasingly sophisticated. While this is true on one level, the view is based on a fundamental misconception: that the nature of hacking has changed. It has not. Any evolution in hacking techniques has been driven more by opportunity than by any change in the nature of the hacker. This article will argue the following: Hackers have changed very little since the 1980s (there have always been moral and immoral hackers) Hacking technologies have changed very little (they have always been the minimum necessary) Motivations have changed very little (it has always been for fun or profit) Opportunities have changed dramatically. It is response to opportunities that has molded and will continue to mold hacking techniques. As opportunities emerge, hackers will evolve. In the Beginning… The early days of hacking are described by Paul Field in his book A British Hacker in America: The Story of PMF & ‘Operation Cybersnare’. The story starts with the arrival of the first microcomputers in schools, at a time when the kids knew as much as their teachers and frequently outperformed them. As a schoolboy, Field was driven by a desire to get the computer to do more than the supplier allowed. “Most early games used [a] type of protection, a system called ‘locking’ the file, so you could only run the program. You couldn’t load it and modify it. Just run it”, he writes. So Field hacked it – a process and motivation that is conceptually no different than jailbreaking an iPhone – to enable and allow more than Apple intended some 25 years later. In the early days there were few opportunities to make money from hacking. Mostly it was just pirating games and other programs for personal use and trade. Again, this continues today. By the time Field left school, the internet was growing; but the web hadn’t begun. Communication was by voice telephony or by dialing in to remote private bulletin boards. This was expensive – especially if, like Field, you lived in the UK and the BBS [bulletin board system] was in America. He, along with many others, used their computing skills to phreak – hacking the telephone system to get free connections. Even then, phreaking wasn’t always just for personal consumption. Field’s book describes his involvement in Operation Cybersnare, the US Secret Service’s first sting operation against ‘hackers’ in 1995. Field had moved to the US, and his reputation among hackers was high. Nevertheless, he was busted. Field worked with the Secret Service – on the proviso that he wouldn’t give up any of his friends. Together they set up the snare, a BBS called Celco 51, with a Secret Service ‘trap and trace’ on all of the telephone lines. When the time came, writes Field, “There was a lot of commotion as each of the arrests went down, and I was glad to see only the people who were committing the crimes for financial gain were being arrested.” Evidently, as early as 1995, hackers were hacking for profit, and law enforcement was setting up elaborate stings to catch them. Nothing much has changed beyond the scale of opportunity and the complexity of the challenge. That scale changed with the emergence of the World Wide Web and ecommerce around the turn of the century, and the complexity increased with the improving security of the software industry around 2005. “Early on”, explains HD Moore, CTO of vulnerability management specialist Rapid7 and founder of Metasploit, “attacks were driven by silly things like curiosity, ego, and vengeance. As the internet became a critical component of our lives, the criminal element has found ways to extract money.” Phi Beta Hacker Independent security researcher and expert Graham Cluley divides the hacking fraternity into three basic categories: hobbyists, criminals and spooks. They each appear to have their own ‘era’ in the evolution of hacking, but the reality is that each category has always existed, and each category still exists today. It is the environment rather than the hacker that has changed. Hobbyists, like the young Field, were the first on the scene. Some evolved into the early virus writers: a few were destructive, but most were in it for the kudos. “There was a badge of honor in honing code over many, many months that would prove difficult for anti-virus vendors to detect”, explains Cluley. “The ‘coolness’ of malware would be measured by the millions of mutations its polymorphic engine could produce, rather than the millions of dollars it might bring to its maker.” Then came the criminals, who quickly realized that viruses and stealthier trojans could be used to make money via fraud. “Fake anti-virus attacks, ransomware, keyloggers and spyware were produced en masse”, Cluley recalls. “In addition, organized criminals oversaw the rise of the botnet – a way of monetizing millions of PCs, by ordering them to launch a DDoS [distributed denial-of-service] attack or spread spam campaigns.” Now we have the spooks engaged in state-sponsored cyber espionage and warfare. We think cyber spies are new, but it is naive to think so; we think cyber war is new, but all governments have been exploring it for many years. In both cases it is cheaper, safer, and potentially more effective than traditional real-world methods. |